Log in with an SSH private key on Linux and macOS
- A tutorial on configuring SSH Server to Authenticate with Private/Public Keys using Ubuntu Linux http://www.danscourses.com/Linux-Fundamentals/how.
- There are two kinds of keys: Server or host keys, which identify the server to the user, and user keys, which allow logging in. The private host key of the server is stored in /etc/ssh/. The corresponding public key is automatically added (after a prompt) to knownhosts in /.ssh on the client.
$ ssh-keygen On execution, we are prompted to specify a file in which to save the private key, the default being /home/user/.ssh/idrsa; here idrsa is the name of our Private Key file. You can always specify a different path and name for the Private Key file. For our demonstration, we.
Authored by: Brint Ohearn
This article demonstrates how to use a private key to log in to a Linux®server by using a private key with a Terminal session on macOS®. However,you can follow the same process to use a private key when using anyterminal software on Linux.
Note: For information about using Secure Shell (SSH) private keys on Microsoft®Windows® operating systems, seeLogging in with an SSH Private Key on Windowsand Generate RSA keys with SSH by using PuTTYgen.
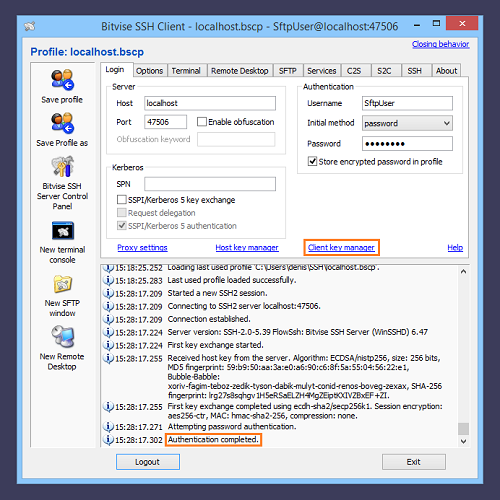
Prerequisites
To complete this process, you need the following software applications:
- SSH client software that is installed on your Linux or macOS operating system by default.
- Your favorite text editor. This example uses the vim text editor.
- Your private key. For more information about generating a key on Linux or macOS, seeConnect to a server by using SSH on Linux or Mac OS X.
Log in with a private key
Using a text editor, create a file in which to store your private key. This example usesthe file deployment_key.txt.
To edit the file in vim, type the following command:
After the editor starts, press i to turn on insert mode.
Paste your private key, such as the one in the following image, into the file.Be sure to include the BEGIN and END Mcdonald's twitter campaign backfires. lines.
To save your changes, press Esc.
Type :wq to write the file and return to the command line.
Run the following command to change the file permissions to 600 to secure the key. You can also set them to 400.This step is required:
Use the key to log in to the SSH client as shown in the following example, which loads the key in file deployment_key.txt, and logs in as user demo to IP 192.237.248.66:
When you are prompted to confirm the connection, type yes and then press Enter.
If your SSH key requires a password, enter it when prompted to complete the connection.
Share this information:
©2020 Rackspace US, Inc.

Except where otherwise noted, content on this site is licensed under a Creative Commons Attribution-NonCommercial-NoDerivs 3.0 Unported License
In every SSH/SFTP connection there are four keys (or two key-pairs) involved. This article explains a difference between them and what keys an SFTP client user needs to care about.
The SSH employs a public key cryptography. A public-key cryptography, also known as asymmetric cryptography, is a class of cryptographic algorithms which requires two separate keys, one of which is secret (or private) and one of which is public.1 Together they are known as a key-pair. In SSH, the public key cryptography is used in both directions (client to server and server to client), so two key pairs are used. One key pair is known as a host (server) key, the other as a user (client) key.
A user private key is key that is kept secret by the SSH user on his/her client machine. The user must never reveal the private key to anyone, including the server (server administrator), not to compromise his/her identity.
Ssh Private Key Password
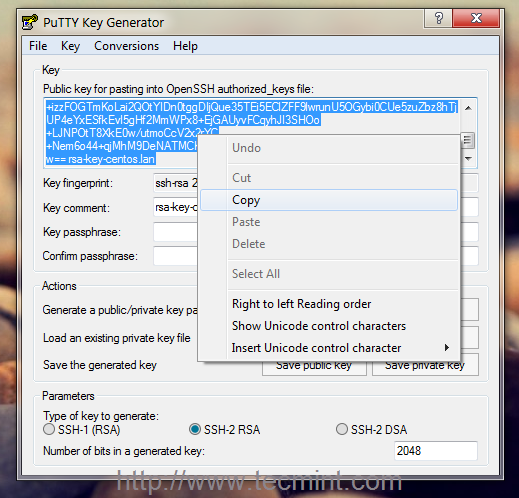
To protect the private key, it should be generated locally on a user’s machine (e.g. using PuTTYgen) and stored encrypted by a passphrase. The passphrase should be long enough (that’s why it’s called passphrase, not password) to withstand a brute-force attack for a reasonably long time, in case an attacker obtains the private key file. Espresso mac.
Different file formats are used to store private keys. WinSCP supports PuTTY format, with .ppk extension.
A user public key is a counterpart to user private key. They are generated at the same time. The user public key can be safely revealed to anyone, without compromising user identity.
To allow authorization of the user on a server, the user public key is registered on the server. In the most widespread SSH server implementation, the OpenSSH, file ~/.ssh/authorized_keys is used for that.
Ssh To Server With Private Keyword
Learn more about public key authentication in general and how to setup authentication with public keys.
Advertisement
Ssh Using Private Key
A host private key is generated when the SSH server is set up. It is safely stored in a location that should be accessible by a server administrator only. The user connecting to the SSH server does not need to care about host private key in general.
A host public key is a counterpart to host private key. They are generated at the same time. The host public key can be safely revealed to anyone, without compromising host identity.
To allow authorizing the host to the user, the user should be provided with host public key in advance, before connecting. The client application typically prompts the user with host public key on the first connection to allow the user to verify/authorize the key. The host public key is then saved and verified automatically on further connections. The client application warns the user, if the host key changes.
- The text is partially copied from Wikipedia article on Public-key cryptography. The text is licensed under GNU Free Documentation License.Back
